|

Cyber security expert Cyrill Brunschwiler gives some advice on cyber security for family offices ranging from passwords, non-computer devices, the right cloud solutions to the weakest links.Brunschwiler is managing director at Compass Security, a cyber security firm with offices throughout Switzerland and in Berlin. Opalesque: What recommendations would you make to family offices regarding cyber security? Cyrill Brunschwiler: If you consider the business case of a family office, it does not differ much from an investment company or trust. However, contact in a family office is very personal and this is of course a good prerequisite for recognizing social engineering attacks. Basically, one can say that families that are in the public eye have an increased risk. But in most cases, family offices hardly differ from other service providers in terms of their IT infrastructure and are therefore also susceptible to the same threats such as infiltration by Trojan horses or against encryption of documents by Ransomware. Opalesque: Anything they should not do? Cyrill Brunschwiler: People often use the same password everywhere. That is a severe problem. Some time ago, a Swiss online merchant was accused of losing usernames and passwords after it was found that many valid login attempts were made for Swiss accounts from foreign locations. It then turned out that the same several thousand accounts had been lost at another company. Obviously, the users had the same username (email address) and password. For the hacker, it is clear as daylight that if you have an email address ending in “ch”, you probably also have an account with the major Swiss online shops. For this reason, you should use different passwords. Opalesque: What about security when using multiple devices? Cyrill Brunschwiler:Smartphones and tablets are very different from standard computers. Each application is isolated in itself. This is also called a sandbox. Therefore, the apps cannot easily access files from other apps. It is safer to do your online banking on the iPad than on your laptop because it is much more difficult to infect such a device with malware. Zerodium, a company that specializes in dealing with vulnerabilities, buys information on identified vulnerabilities and on how to exploit them. Subscribers to Zerodium’s feed get that information to tailor defence and offense tactics. Currently, $0.5 million is claimed to be paid for a vulnerability that allows full control over the Windows operating system. In comparison, $1.5 million is offered for the same functionality on the Apple iOS platform. The amount of these bounties confirms the claim and give an idea of how difficult it really is to remotely control a mobile device without user intervention. Opalesque: Cloud solutions, how secure are they? Cyrill Brunschwiler: The term cloud is ambiguous. I understand “cloud” to mean that you no longer know exactly where the service is running; it could be in an Irish data center in the morning, then in the room next door in the afternoon and in a Japanese data center at night. Since the services are partly operated in foreign jurisdictions, data protection laws are a central issue. Maybe you do not want your data to be in a foreign location. Luckily, large cloud providers have started to set up Swiss data centers - where the cloud data is then stored in Switzerland. I recommend every small business to opt for cloud-based services at one of the mayor players like Amazon, Microsoft, Google or Alibaba, if data protection and privacy requirements permits. The big ones employ very reputable cyber security teams that are responsible for the entire infrastructure on a permanent basis. You will never get such service from a niche or local provider. Access regulations are the most important things to consider when using cloud services. Cloud services can be used from anywhere in the world. Following that, corporate data can be accessed with a username and password from outside the company. It is therefore a good idea to protect access with a second factor (e.g. SMS or app) as is the case with e-banking. In addition, you should keep a watchful eye on those who leave your company. It is imperative that the permissions of resigned employees are immediately revoked. Opalesque: Business and outsourcing partners: what security risks do they pose? Cyrill Brunschwiler: Business partners are often imitated in social engineering attacks. This means forging documents with the CI/CD of the business partner or sending forged emails with the sender for example. “Keep a simple rule in mind. The attacker takes the path of least resistance. So, all elements in the chain have to be secured.” Currently, attackers use cracked email accounts to send fake invoices or money orders to the accounts’ business partners. It even happens that hackers delete an invoice from the inbox, modify the PDF such as providing it with a different IBAN (International Bank Account Number) and put the forged invoice back into the inbox. We have observed and analyzed quite a number of such cases this year. We are talking large 6-digit amounts. The ROI of such an attack is both absolutely fantastic and totally scary. Whenever you consider investments into measures, keep a simple rule in mind. The attacker takes the path of least resistance. If a company is difficult to attack, then perhaps the IT service provider poses an easy gateway to the company. So, all elements in the chain have to be secured - because a chain is only as b as its weakest element. Thus, do not put all your money on a single bet. 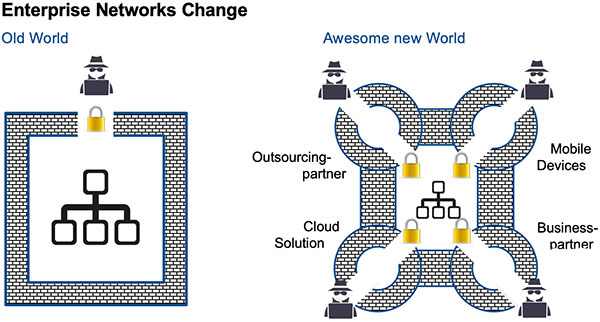
Opalesque: Could you give us an example of a past family office cybercrime that can serve as a warning? Cyrill Brunschwiler: We worked on a case this spring where the company’s core database was encrypted by a standard Ransomware. A decryption of the data was not possible as the backup got encrypted too. As a result, the external IT service provider did not have any hope of recovering the data and started formatting the system. Fortunately, one of the hard disks was corrupt and we were able to reconstruct the database from shadow data over the weekend. On top of that, my colleagues had to restore the application, because the manufacturer did not have that specific version anymore. This example shows the potential that certain companies have when it comes to cyber security. | ||||
|
Horizons: Family Office & Investor Magazine
Cybersecurity – Expert entreats: Do NOT use the same password |
|





 RSS
RSS